With Dynamic Gateways
Before continuing, please checkout the first instance of this configuration here where we use the same logic but our gateways are configured statically. The priciple here is the same however how we update the distance of the routes in a failover scenario is different as well as how we get the next-hop IP (dynamically)
The Ultimate MikroTik Internet Failover #1
Routing
The routing table will be propulated dynamically and as our PPPoE interface is the backup it will be blue.
The only static route we need is the one to allow ether1 to check when 8.8.8.8 becomes accessible again. We add this static route to point to the gateway for ether1 however as we’re receiving this gateway dynamically we need update this route should our WAN1 (ether1) next-hop IP (gateway) change. This is achieved via the DHCP Client script outlined next
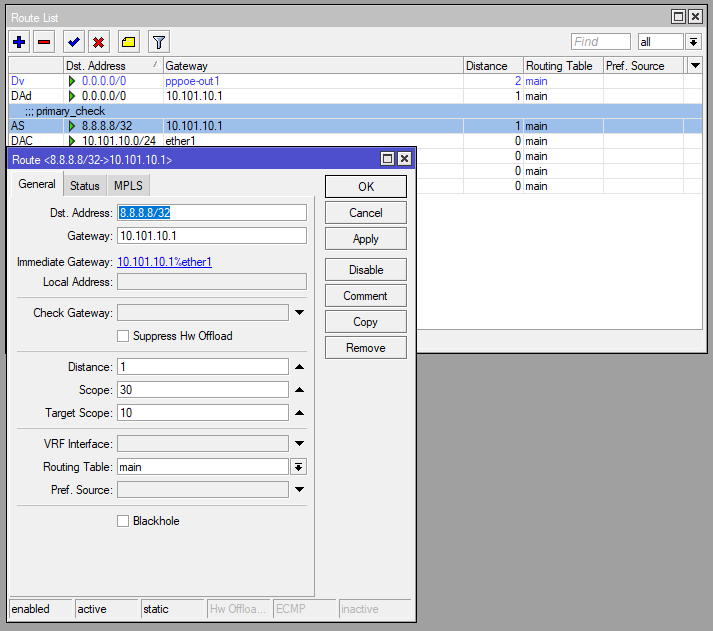
DHCP Client
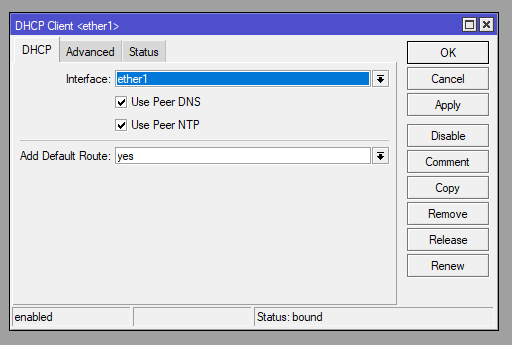
The DHCP Client is set on ether1 to receive our WAN IP and Default gateway, which in our previous guide was a static IP and default route.
With this we need to utilise the Script function within the client. When changes are made to the dhcp-client (enabled/disabled) it runs so the script will confirm there is a bound IP address and uses the received GW IP to update the primary_check static route as mentioned in the Routing seciton above.
WAN1
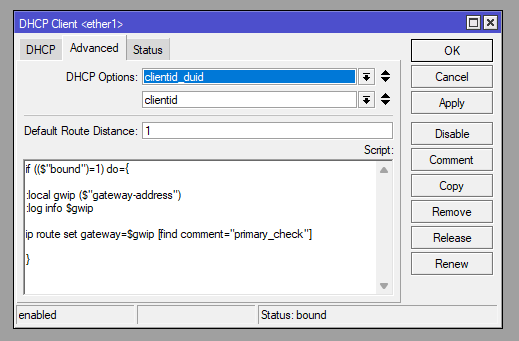
if (($"bound")=1) do={
:local gwip ($"gateway-address")
:log info $gwip
ip route set gateway=$gwip [find comment="primary_check"]
}/ip dhcp-client
add dhcp-options=clientid_duid,clientid interface=ether1 script="if ((\$\"bound\")=1) do={\r\
\n\r\
\n:local gwip (\$\"gateway-address\")\r\
\n\r\
\nip route set gateway=\$gwip [find comment=\"primary_check\"]\r\
\n\r\
\n}"WAN2
As with WAN1, this interface gets it’s IP dynamically, but unlike WAN1, this one is via PPPoE.
In this interface by default the Add Default Route is enabled but we will change the Distance to 2. This means this default route will be a secondary/backup route.
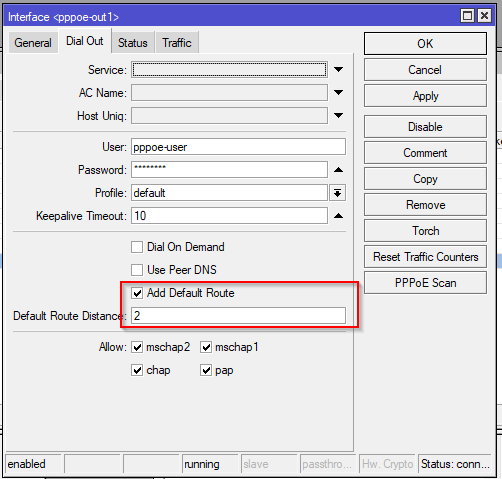
/interface pppoe-client
add add-default-route=yes default-route-distance=2 disabled=no interface=ether2 name=pppoe-out1 user=pppoe-userNetwatch
The Netwatch tool pings 8.8.8.8 and when it fails to get a response it run inet_check script. This is then disabled unitl the primary connection is re-established.
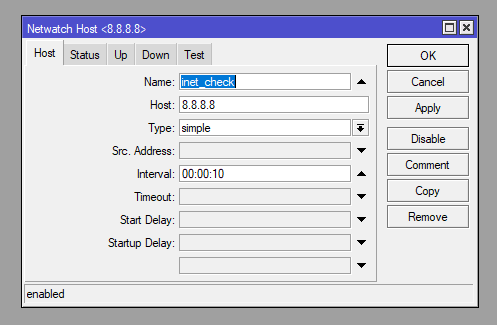
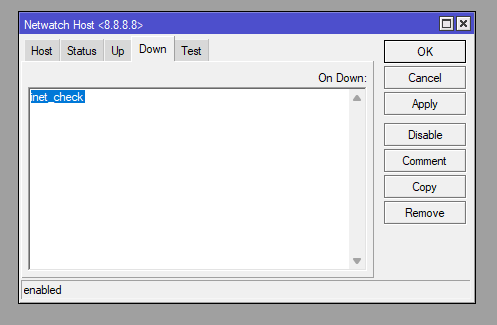
/tool netwatch
add disabled=no down-script=inet_check host=8.8.8.8 http-codes="" interval=10s name=inet_check test-script="" type=simple up-script=""
Scripts
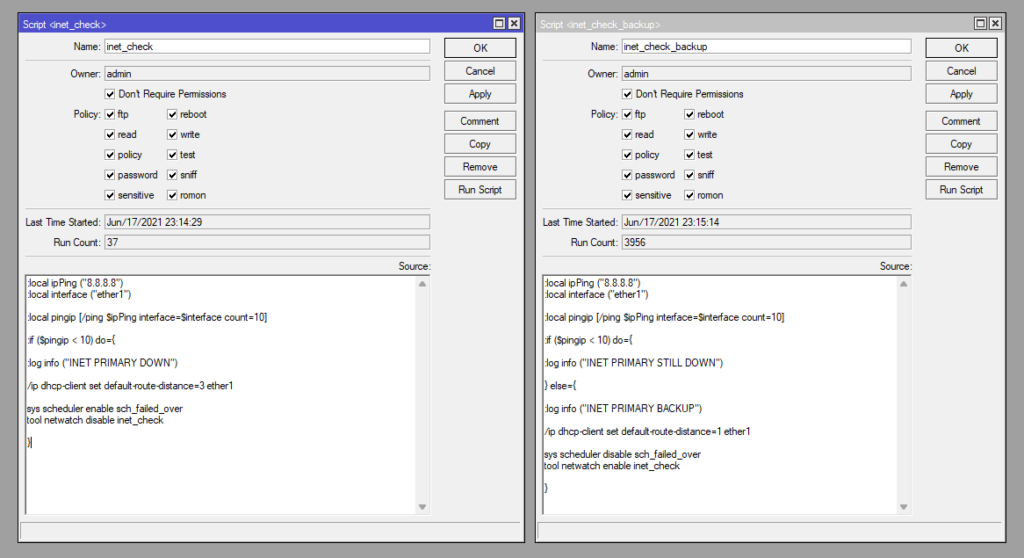
As with the previous guide, we have 2 scripts, the first is run when Netwatch fails to ping our public IP of Google DNS (8.8.8.8). Then follows this process
- Set the following variables:
- ipPing = 8.8.8.8
- interface = ether1
- Run a ping command for 10 pings to the ipPing variable (8.8.8.8) using the interface variable (ether1)
- Using an if statement, if there at less then 10 successful pings do the following
- Add a log entry saying INET PRIMARY DOWN
- Set the DHCP CLIENT for ether1 to have a default gateway distance of 3
- Enable the Scheduler called sch_failed_over
- Disable the Netwatch called inet_check
Then the second scripted is run as per the newly enabled scheduler (enabled as part of inet_check script):
- Set the following variables:
- ipPing = 8.8.8.8
- interface = ether1
- Run a ping command for 10 pings to the ipPing variable (8.8.8.8) using the interface variable (ether1)
- Using an if statement, if there at less then 10 successful pings do the following
- Add a log entry saying INET PRIMARY STILL DOWN
- If the If statement is false (receives 10 sucessful replies) do the following:
- Set the DHCP CLIENT for ether1 to have a default gateway distance of 1
- Disable the Scheduler called sch_failed_over
- Enable the Netwatch called inet_check
:local ipPing ("8.8.8.8")
:local interface ("ether1")
:local pingip [/ping $ipPing interface=$interface count=10]
:if ($pingip < 10) do={
:log info ("INET PRIMARY DOWN")
/ip dhcp-client set default-route-distance=3 ether1
sys scheduler enable sch_failed_over
tool netwatch disable inet_check
}:local ipPing ("8.8.8.8")
:local interface ("ether1")
:local pingip [/ping $ipPing interface=$interface count=10]
:if ($pingip < 10) do={
:log info ("INET PRIMARY STILL DOWN")
} else={
:log info ("INET PRIMARY BACKUP")
/ip dhcp-client set default-route-distance=1 ether1
sys scheduler disable sch_failed_over
tool netwatch enable inet_check
}/system script
add dont-require-permissions=yes name=inet_check_backup owner=admin policy=ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source=":lo\
cal ipPing (\"8.8.8.8\")\r\
\n:local interface (\"ether1\")\r\
\n\r\
\n:local pingip [/ping \$ipPing interface=\$interface count=10]\r\
\n\r\
\n:if (\$pingip < 10) do={\r\
\n\r\
\n:log info (\"INET PRIMARY STILL DOWN\")\r\
\n\r\
\n} else={\r\
\n\r\
\n:log info (\"INET PRIMARY BACKUP\")\r\
\n\r\
\n/ip dhcp-client set default-route-distance=1 ether1\r\
\n\r\
\nsys scheduler disable sch_failed_over\r\
\ntool netwatch enable inet_check\r\
\n\r\
\n\r\
\n}"
add dont-require-permissions=yes name=inet_check owner=admin policy=ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source=":local ipP\
ing (\"8.8.8.8\")\r\
\n:local interface (\"ether1\")\r\
\n\r\
\n:local pingip [/ping \$ipPing interface=\$interface count=10]\r\
\n\r\
\n:if (\$pingip < 10) do={\r\
\n\r\
\n:log info (\"INET PRIMARY DOWN\")\r\
\n\r\
\n/ip dhcp-client set default-route-distance=3 ether1\r\
\n\r\
\nsys scheduler enable sch_failed_over\r\
\ntool netwatch disable inet_check\r\
\n\r\
\n}"Scheduler
The Scheduler is disabled by default and gets enabled by the inet_check script should the 10 pings to 8.8.8.8 fail. This scheduler then runs the inet_check_backup script every 10 seconds until it gets disabled due to ether1 being able to ping 8.8.8.8 again.
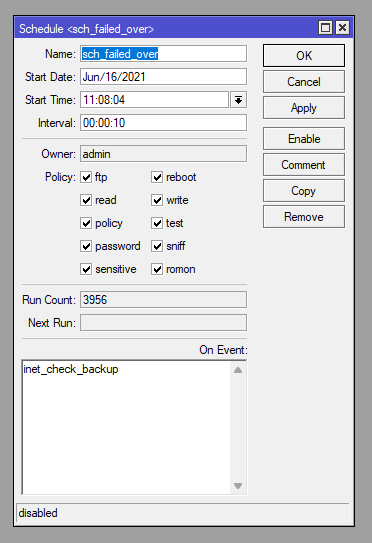
/system scheduler
add disabled=yes interval=10s name=sch_failed_over on-event=inet_check_backup policy=ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=2021-06-16 start-time=11:08:04


Awesome job on “The Ultimate MikroTik Internet Failover #2”
I have been looking for this for years and avoided mikrotik if the use case needed failover. Most examples on the forums and wiki are over complicated and don’t work correctly. This is perfect!
Thanks so much!
That’s great, I’m happy it was useful. If there’s anything you’re struggling to find a guide on let me know and I’ll see if I can help!