Option 1: Mangle Rules
To achieve policy based routing on a MikroTik, this option leverages mangle rules to match the source traffic and then marks the traffic with a new routing mark which corresponds to a new FIB routing table. The traffic then gets routed by new routes (in our case a new default route) created for this new routing table. The source is applied via address lists so any additional hosts/networks can be added simply via a new entry to the list and no additional mangle rules required.
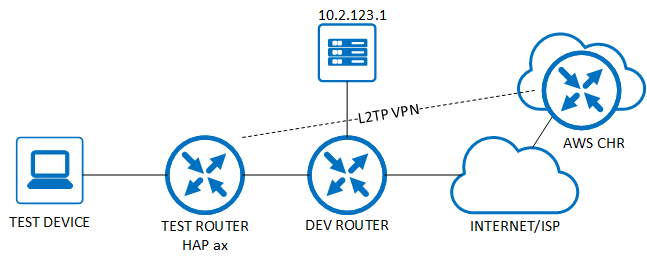
As above our topology has a client machine (192.168.123.150) connected to the Test router (hAP ax), which has internet access via the Dev Network. There is then a L2TP IPSEC VPN setup between the Test router and the AWS CHR. The L2TP IP on the CHR is 10.1.254.1 and the client (Test Router) is 10.1.254.100. This gives us 2 interfaces to route out of: the internet uplink (ether 1 – 10.2.0.1) and the L2TP interface (l2tp-client1 – 10.1.254.100).
New FIB Routing Table
Create a New Routing Table (Routing > Table)
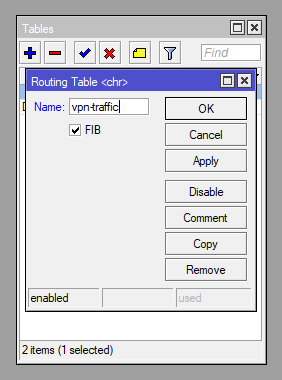
/routing table
add disabled=no fib name=vpn-trafficAddress Lists
Create an Address List (IP > Firewall > Address Lists) for the host(s)/subnet you want to route over your VPN or other interface. Give it an identifying name and use the same name in the dropdown for all other hosts.
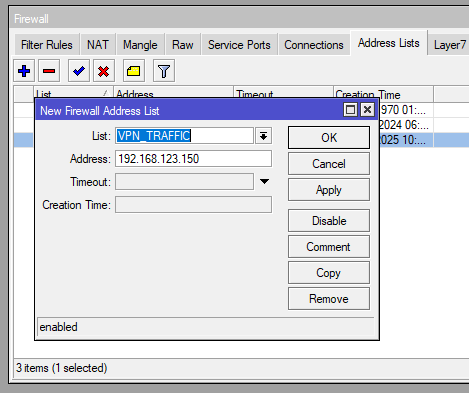
/ip firewall address-list
add address=192.168.123.150 list=VPN_TRAFFICNow create a different address list for all the subnets you don’t want to route via the tunnel/separate interface (including the subnet of the host). For example our host is 192.168.123.150/24 so we need to include 192.168.123.0/24.
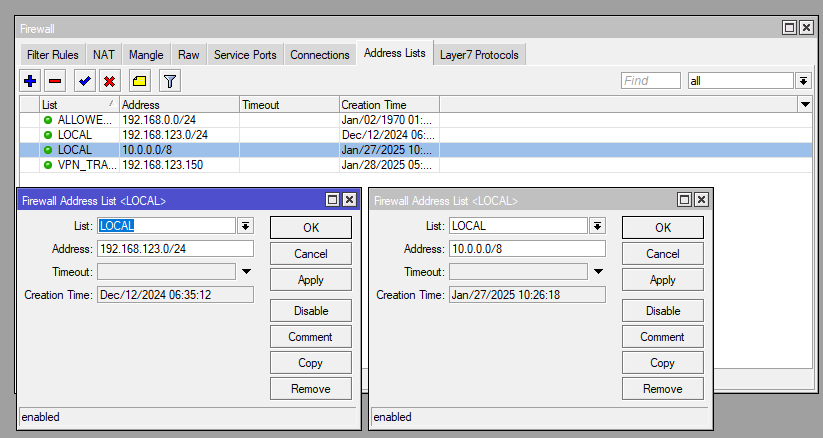
/ip firewall address-list
add address=192.168.123.0/24 list=LOCAL
add address=10.0.0.0/8 list=LOCALMangle Rules
Now we create our Mangle Rules (IP > Firewall > Mangle) to mark our traffic. Use prerouting and in the Src Address List use the firest address list (the hosts we want to route) and for the Dst. Address List use the other list but click the ! so it negates it. This means we are routing all traffic except anything in our Address List call LOCAL.
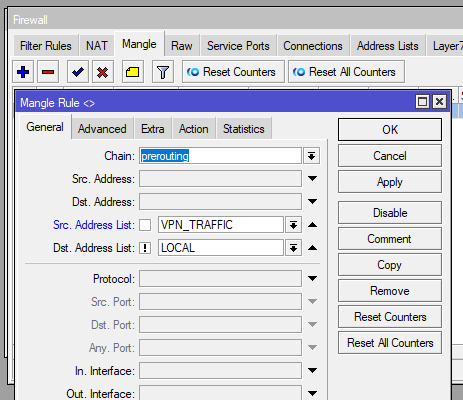
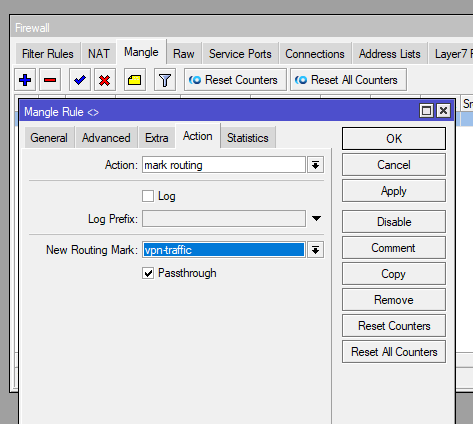
Routing Table – Default Route
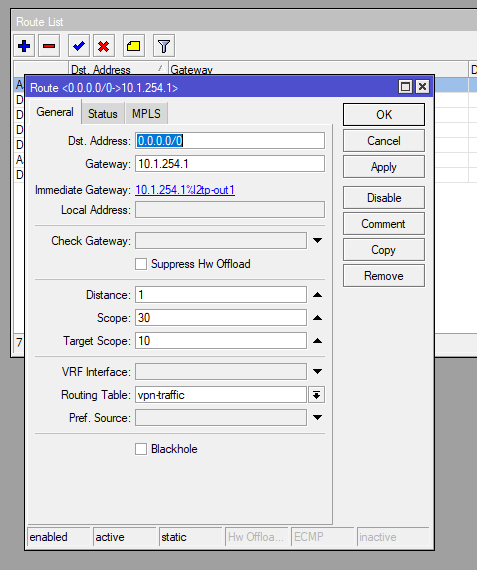
Now the last step is to create a new default route using our VPN interface/IP or whichever interface you are routing to, and in the Routing Table select our other Routing Table (called vpn-traffic)
Option 2: Routing Rules
This setup is similar to the first option, however we use a Routing Rule to steer our traffic. It is a quicker and easier setup however it does limit the scalability of the other solution as it requires us to create a rule per client/network, where as we can achieve this with the address lists in the mangle rule option.
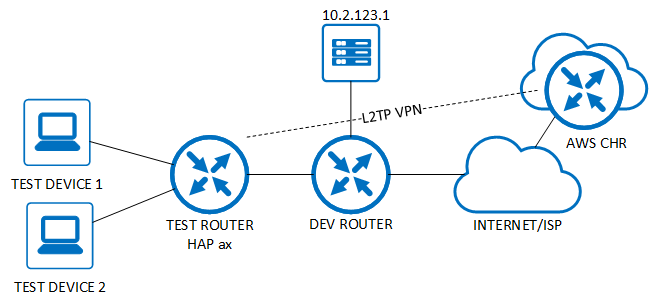
As above our topology is the same, where the client machine (192.168.123.150) is connected to the Test router (hAP ax) and has internet access via the Dev Network. There is then a L2TP IPSEC VPN setup between the Test router and the AWS CHR. The L2TP IP on the CHR is 10.1.254.1 and the client (Test Router) is 10.1.254.100. This gives us 2 interfaces to route out of: the internet uplink (ether 1 – 10.2.0.1) and the L2TP interface (l2tp-client1 – 10.1.254.100).
In the above video there was an additional testing machine which is included in the above topology, however wasn’t shown in the video so has been added here for some clarity.
New FIB Routing Table
As with the first option (mangle rules), we add an additional routing table (Routing > Table)

Routing Rules
Then we create our rule (Routing > Rules) to match our host IP/subnet and then specify the destination (in our case using a default route of 0.0.0.0/0) and finally specify the new routing table created above.

Routing Table – Default Route
Last step is then to create our new default route for our new routing table (IP > Routes), specifying the next hop (which in this case is IP address of the remote side L2TP interface) and then select the route to exist in the new Routing Table (vpn-traffic).