For the Latest Deals on MikroTik products click here!
Introduction to MikroTik IPsec and GRE Tunnel Configuration
IPsec (Internet Protocol Security) is a suite of protocols that provides secure communication over an IP network by encrypting and authenticating the packets between devices. It is widely used for setting up secure VPNs, ensuring data integrity, confidentiality, and authenticity.
On the other hand, a GRE (Generic Routing Encapsulation) tunnel is a simple, point-to-point connection that encapsulates a wide variety of network layer protocols inside IP packets. GRE is often used to connect remote networks as though they were directly connected to the same physical network.
When combined, GRE over IPsec provides the benefits of both secure communication and the flexibility of GRE. This setup is ideal for scenarios where you need to pass routing protocols (such as OSPF or BGP) or non-IP traffic over a secure connection between two sites.
Benefits of Using GRE over IPsec
- Encryption and Security: IPsec ensures data confidentiality and integrity.
- Protocol Flexibility: GRE supports multiple protocols (not just IP).
- Dynamic Routing: GRE allows the use of dynamic routing protocols, which simplifies network management.
- Traffic Separation: GRE can encapsulate traffic, keeping it isolated and organised.
Click Here to view how to configure a MikroTik CHR in AWS using the Free Tier
Site A: CHR-AU
Bridge
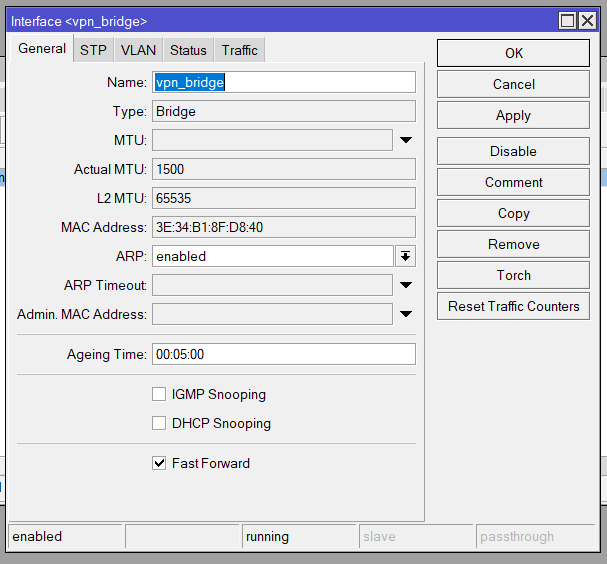
/interface bridge
add name=vpn_bridge protocol-mode=none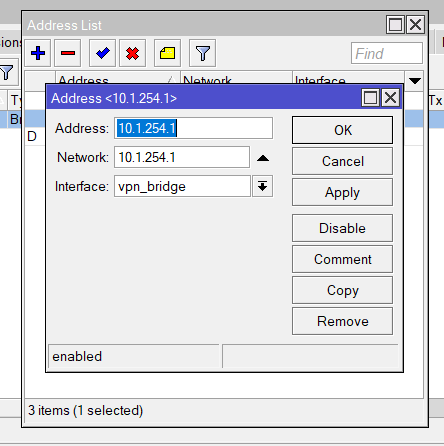
/ip address
add address=10.1.254.1/24 interface=vpn_bridge network=10.1.254.0IPSec Tunnel
Go to IP > IPsec and on the Profile tab add a new profile, using the following settings, leaving the rest default:
| Name: profile-ipsec Hash Algorithms: sha256 Encryption Algorithm: aes-256 DH Group: modp2048 (14) |
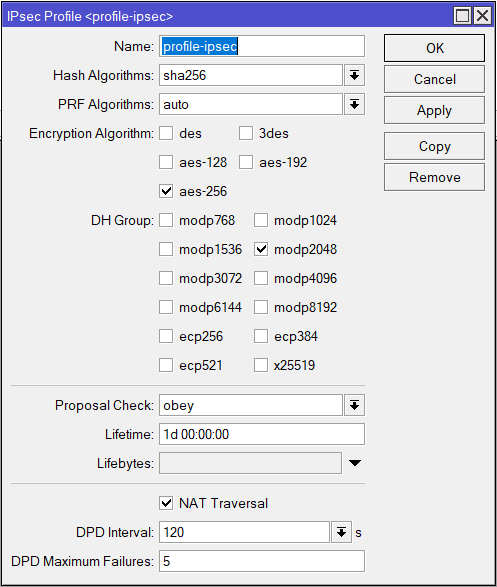
/ip ipsec profile
add dh-group=modp2048 enc-algorithm=aes-256,3des hash-algorithm=sha256 name=profile-ipsecNext click on the Peer tab, add the following:
| Name: chr-uk Address: 18.132.39.216 (the IP address of the remote end) Profile: profile-ipsec Exchange Mode: IKE2 |
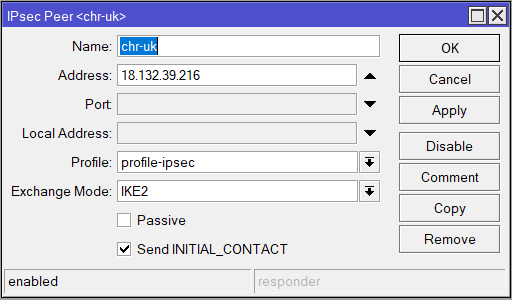
/ip ipsec peer
add address=18.132.39.216/32 exchange-mode=ike2 name=chr-au profile=profile-ipsecThen the Proposal:
| Name: proposal-ipsec Auth. Algorithms: sha256 Encr. Algorithms: aes-256 cbc PFS Group: modp2048 |
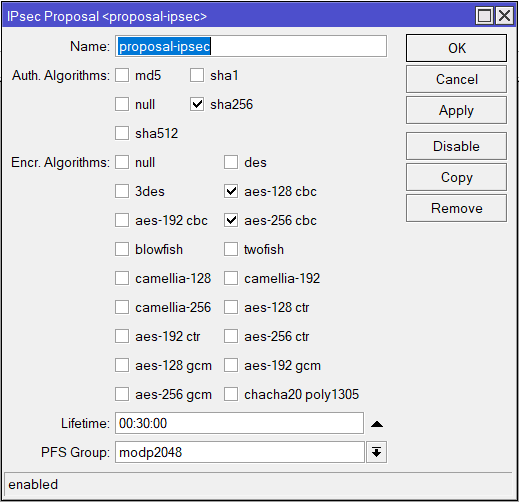
/ip ipsec proposal
add auth-algorithms=sha256 name=proposal-ipsec pfs-group=modp2048Then the Identity:
| Name: chr-uk Auth. Method: pre shared key Secret: helloworld123 (use a secure password) |
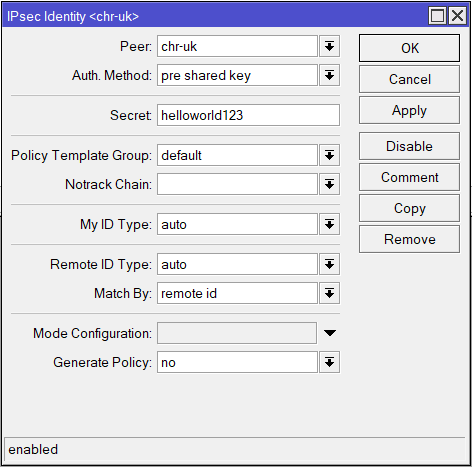
/ip ipsec identity
add peer=chr-uk secret=helloworld123Finally the Policy:
| General | Action |
| Peer: chr-uk Tunnel: yes Src. Address: 10.1.254.0/24 Dst. Address: 10.2.254.0/24 | Level: unique |
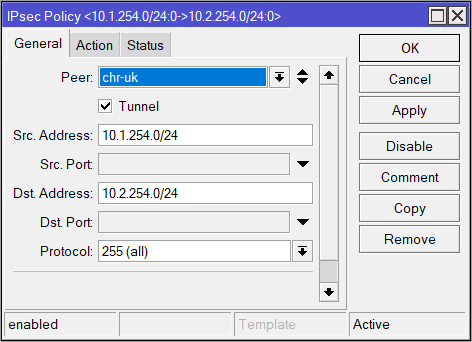
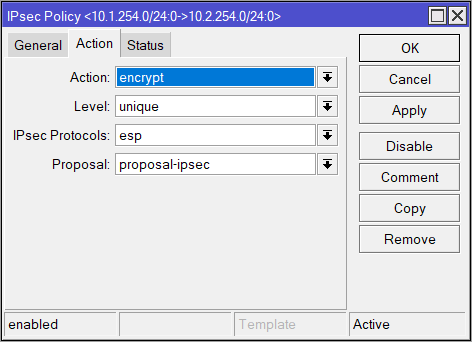
/ip ipsec policy
add dst-address=10.2.254.0/24 level=unique peer=chr-uk proposal=proposal-ipsec src-address=10.1.254.0/24 tunnel=yes No-NAT
IP > Firewall > NAT
| General | Action |
| Src. Address: 10.1.254.0/24 Dst. Address: 10.2.254.0/24 | Action: accept |
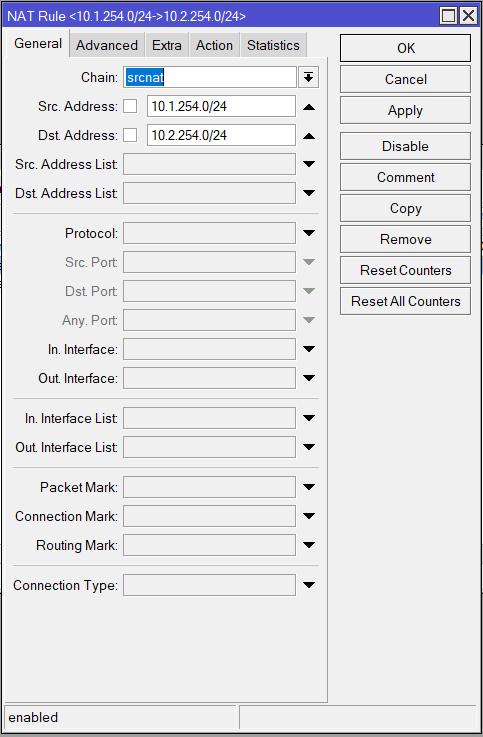
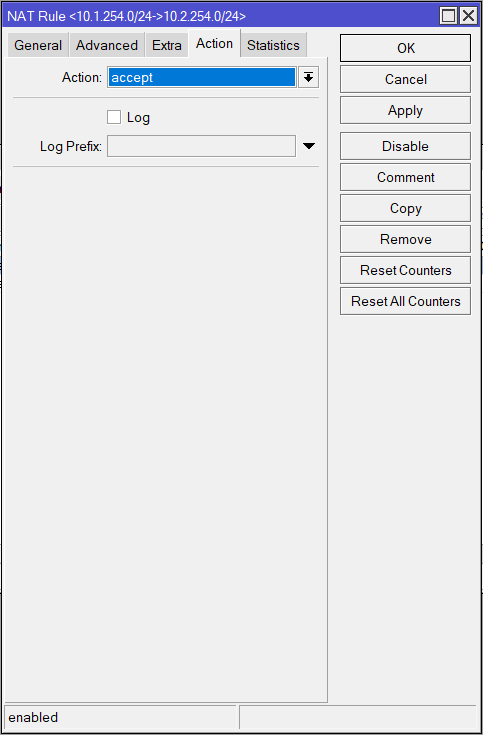
/ip firewall nat
add action=accept chain=srcnat dst-address=10.2.254.0/24 src-address=10.1.254.0/24GRE Tunnel
Interface + GRE Tunnel
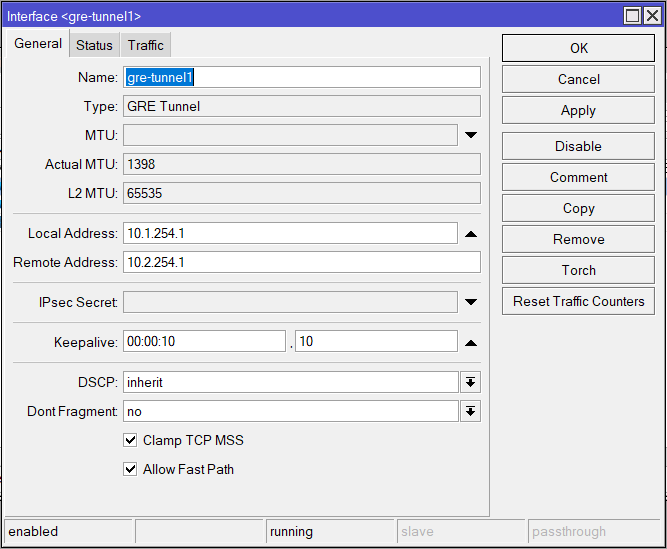
/interface gre
add local-address=10.2.254.1 name=gre-tunnel1 remote-address=10.1.254.1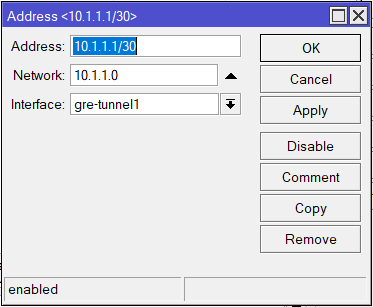
/ip address
add address=10.1.1.1/30 interface=gre-tunnel1 network=10.1.1.0Site B: CHR-UK
Bridge
add name=vpn_bridge protocol-mode=none/ip address
add address=10.2.254.1/24 interface=vpn_bridge network=10.2.254.0IPSec Tunnel
/ip ipsec profile
add dh-group=modp2048 enc-algorithm=aes-256,3des hash-algorithm=sha256 name=profile-ipsec/ip ipsec peer
add address=54.66.163.58/32 exchange-mode=ike2 name=chr-au profile=profile-ipsec/ip ipsec proposal
add auth-algorithms=sha256 name=proposal-ipsec pfs-group=modp2048/ip ipsec identity
add peer=chr-au secret=helloworld123/ip ipsec policy
add dst-address=10.1.254.0/24 level=unique peer=chr-au proposal=proposal-ipsec src-address=10.2.254.0/24 tunnel=yes No-NAT
/ip firewall nat
add action=accept chain=srcnat dst-address=10.1.254.0/24 src-address=10.2.254.0/24GRE Tunnel
/interface gre
add local-address=10.2.254.1 name=gre-tunnel1 remote-address=10.1.254.1/ip address
add address=10.1.1.2/30 interface=gre-tunnel1 network=10.1.1.0Testing
Bridge
CHR-AU
/interface bridge
add name=lan_bridge protocol-mode=noneCHR-UK
/interface bridge
add name=lan_bridge protocol-mode=noneAddress
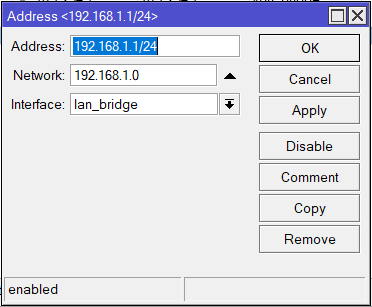
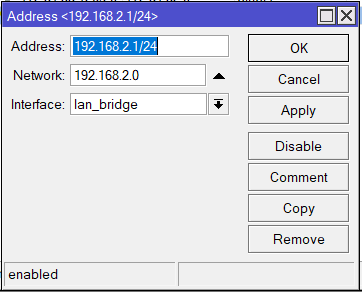
CHR-AU
/ip address
add address=192.168.2.1/24 interface=lan_bridge network=192.168.2.0CHR-UK
/ip address
add address=192.168.2.1/24 interface=lan_bridge network=192.168.2.0Static Routes
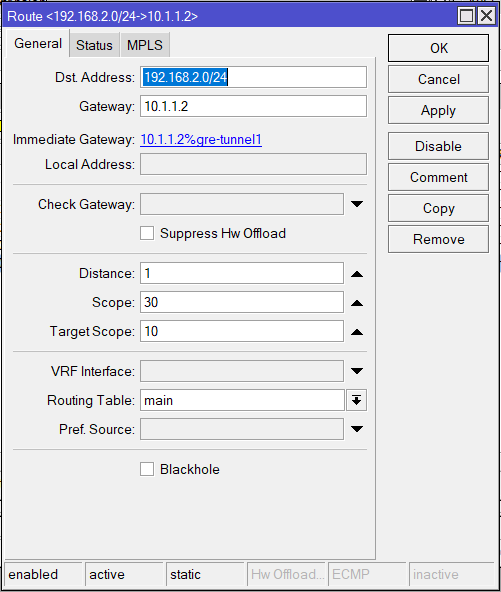
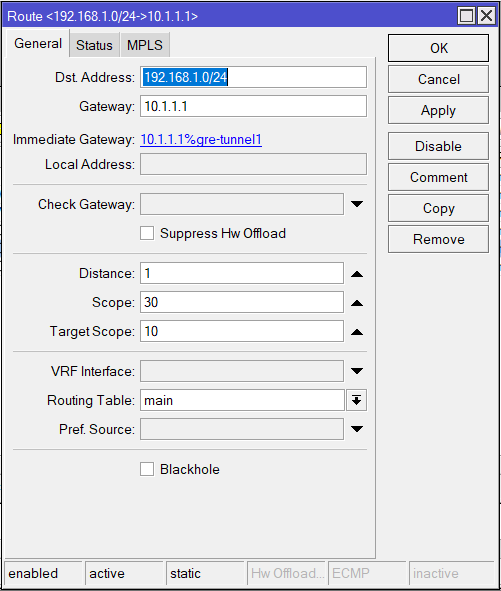
CHR-AU
/ip route
add disabled=no dst-address=192.168.1.0/24 gateway=10.1.1.1 CHR-UK
/ip route
add disabled=no dst-address=192.168.1.0/24 gateway=10.1.1.1