Server Update
Start by updating the software repositories and upgrading the software
sudo apt update
sudo apt upgradeInstall Apache2 (Web Server)
Next we install the Apache2 web server
sudo apt -y install apache2Install PHP
Now the PHP and associated libraries
sudo apt -y install php libapache2-mod-php php-{gd,common,mail,mail-mime,mysql,pear,db,mbstring,xml,curl}Install MySQL Database
For the database we are using MySQL however if you prefer you can use MariaDB
sudo apt -y install mysql-serverConfigure MySQL
Once installed we will configure the database with the following command
sudo mysql_secure_installationThis part is to select the password validation option, which will specify the complexity of the passwords; however, for us we will select NO. This will also mean our root password will be blank. I would recommend setting this afterwards.
Securing the MySQL server deployment.
Connecting to MySQL using a blank password.
VALIDATE PASSWORD COMPONENT can be used to test passwords
and improve security. It checks the strength of password
and allows the users to set only those passwords which are
secure enough. Would you like to setup VALIDATE PASSWORD component?
Press y|Y for Yes, any other key for No: nNow to remove anonymous users: Y
Skipping password set for root as authentication with auth_socket is used by default.
If you would like to use password authentication instead, this can be done with the "ALTER_USER" command.
See https://dev.mysql.com/doc/refman/8.0/en/alter-user.html#alter-user-password-management for more information.
By default, a MySQL installation has an anonymous user,
allowing anyone to log into MySQL without having to have
a user account created for them. This is intended only for
testing, and to make the installation go a bit smoother.
You should remove them before moving into a production
environment.
Remove anonymous users? (Press y|Y for Yes, any other key for No) : y
Success.Prevent ability to log into MySQL using the root password: N
Normally, root should only be allowed to connect from
'localhost'. This ensures that someone cannot guess at
the root password from the network.
Disallow root login remotely? (Press y|Y for Yes, any other key for No) : y
Success.Remove the Test Database and associated privileges: Y
By default, MySQL comes with a database named 'test' that
anyone can access. This is also intended only for testing,
and should be removed before moving into a production
environment.
Remove test database and access to it? (Press y|Y for Yes, any other key for No) : y
- Dropping test database...
Success.
- Removing privileges on test database...
Success.Reloading the privilege tables to make changes take effect: Y
Reloading the privilege tables will ensure that all changes
made so far will take effect immediately.
Reload privilege tables now? (Press y|Y for Yes, any other key for No) : y
Success.MySQL is now setup
All done!Install FreeRADIUS
Now we install FreeRADIUS and required packages
sudo apt -y install freeradius freeradius-mysql freeradius-utils -yTo test the FreeRADIUS installation, first we stop the FreeRADIUS service:
sudo systemctl stop freeradiusThen we run this command to start the service in the foreground so it gives the verbose output. This is also useful when testing and debugging:
sudo freeradius -XListening on auth address * port 1812 bound to server default
Listening on acct address * port 1813 bound to server default
Listening on auth address :: port 1812 bound to server default
Listening on acct address :: port 1813 bound to server default
Listening on auth address 127.0.0.1 port 18120 bound to server inner-tunnel
Listening on proxy address * port 33201
Listening on proxy address :: port 59970
Ready to process requestsConfigure MySQL Database for freeRADIUS
Now we set up the MySQL database for the FreeRADIUS service. As mentioned in the MySQL configuration, our root password will be blank by disabling the validate passwords. After this command and prompted to Enter Password:, just hit enter.
sudo mysql -u root -pOnce in the MySQL, use the following to create the Database and User details.
NB: The database will be named radius, if you want to use a different name change it under the “CREATE DATABASE” part and “GRANT ALL PRIVILEGES ON”
Also the user will be radius too so if you want to use a separate user then change both the “‘radius’@’localhost'” sections
CREATE DATABASE radius;
CREATE USER 'radius'@'localhost' IDENTIFIED by 'helloworld123';
GRANT ALL PRIVILEGES ON radius.* TO 'radius'@'localhost';
FLUSH PRIVILEGES;
quit;Now to for the next bit we need to be root, to do this use the following command
sudo su -This will import the tables needed for FreeRADIUS into our newly created Database
mysql -u root -p radius < /etc/freeradius/3.0/mods-config/sql/main/mysql/schema.sqlThen create a link between these two directories
sudo ln -s /etc/freeradius/3.0/mods-available/sql /etc/freeradius/3.0/mods-enabled/Now we can edit the FreeRADIUS SQL file. To do this we use the nano text editor. User Ctrl + W to search within the file or use the arrow keys to scroll
sudo nano /etc/freeradius/3.0/mods-enabled/sqlChange driver = from rlm_sql_null to rlm_sql_${dialect} but using the # to comment out the first and remove from the second
driver = "rlm_sql_null"
# driver = "rlm_sql_${dialect}"It should now look like this
# driver = "rlm_sql_null"
driver = "rlm_sql_${dialect}"Now change dialect = from sqlite to MySQL
dialect = "sqlite" dialect = "mysql"Now find the ‘mysql {‘ and‘tls {‘ and comment out (add #) to all lines except the warnings = auto
mysql {
# If any of the files below are set, TLS encryption is enabled
tls {
ca_file = "/etc/ssl/certs/my_ca.crt"
ca_path = "/etc/ssl/certs/"
certificate_file = "/etc/ssl/certs/private/client.crt"
private_key_file = "/etc/ssl/certs/private/client.key"
cipher = "DHE-RSA-AES256-SHA:AES128-SHA"
tls_required = yes
tls_check_cert = no
tls_check_cert_cn = no
}
# If yes, (or auto and libmysqlclient reports warnings are
# available), will retrieve and log additional warnings from
# the server if an error has occured. Defaults to 'auto'
warnings = auto
}
It should now look like this
mysql {
# If any of the files below are set, TLS encryption is enabled
#tls {
# ca_file = "/etc/ssl/certs/my_ca.crt"
# ca_path = "/etc/ssl/certs/"
# certificate_file = "/etc/ssl/certs/private/client.crt"
# private_key_file = "/etc/ssl/certs/private/client.key"
# cipher = "DHE-RSA-AES256-SHA:AES128-SHA"
# tls_required = yes
# tls_check_cert = no
# tls_check_cert_cn = no
#}
# If yes, (or auto and libmysqlclient reports warnings are
# available), will retrieve and log additional warnings from
# the server if an error has occured. Defaults to 'auto'
warnings = auto
}Now to add the database details. Locate this section
# Connection info:
#
# server = "localhost"
# port = 3306
# login = "radius"
# password = "radpass"Remove the # from the 4 lines and change the login and password to those set when creating the database. In our example I used the username radius so only the password needed to change.
# Connection info:
#
server = "localhost"
port = 3306
login = "radius"
password = "helloworld123"Now this will be the name of the database we created, however as we used the default name we don’t need to change it
radius_db = "radius"Now find read_clients = yes and uncomment it (remove #)
# read_clients = yes read_clients = yesBy default the table used to manage the Radius clients (the device making the radius request e.g. our MikroTik) is named nas, if you want to change this then it needs to be updated here
client_table = "nas"Now fix some relevant permissions
sudo chgrp -h freerad /etc/freeradius/3.0/mods-available/sql
sudo chown -R freerad:freerad /etc/freeradius/3.0/mods-enabled/sqlFinally restart the FreeRADIUS service
sudo systemctl restart freeradius.serviceInstall PHPMyAdmin
Now to manage our database easierly, we use PHPMyAdmin. To install this run this command
sudo apt install -y phpmyadminNow when prompted, when apache2 is selected (red square in brackets) hit the spacebar to put a *. Then hit TAB and enter on <Ok>
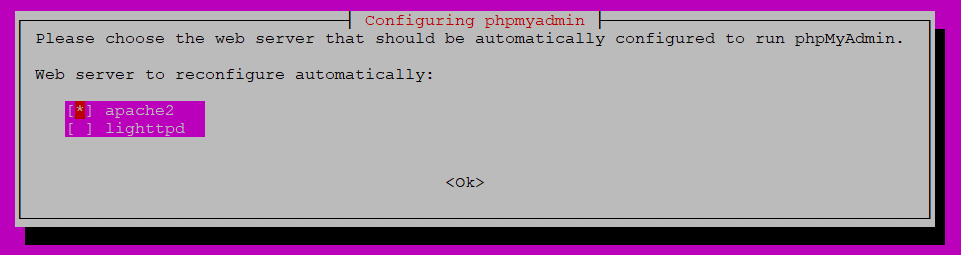
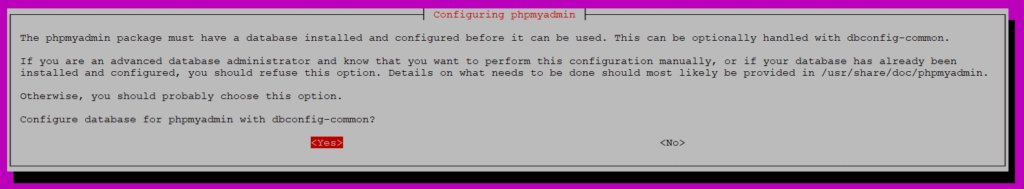
Then when prompted provide a password for the default phpmyadmin database.
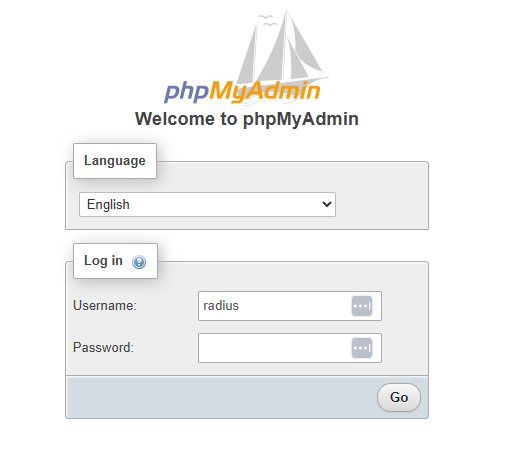
Now once installed go to: https://<IP of Server>/phpmyadmin
Log in with the same details added when created the database (radius / helloworld123)
Now we can add our Radius Client, which is the device that makes radius request, for example the MikroTik device running the service we need radius for (HotSpot, PPPoE Server, CAPsMAN).
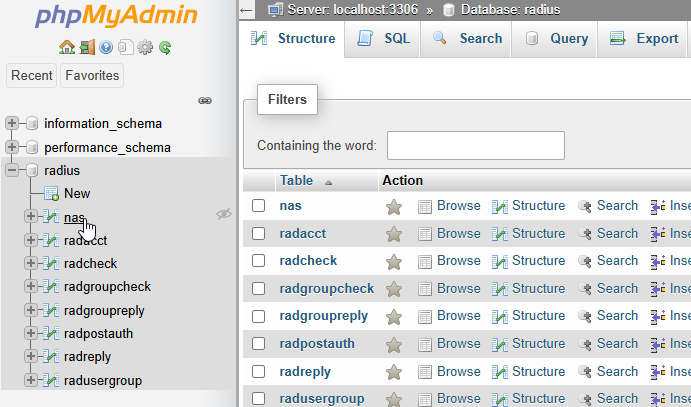
For this we will be testing from a PC so we put that in. To do so we click Insert and add the following:
| nasname: The IP or domain/hostname of the device making the request shortname: A standard descriptive name secret: The secret/password used to validate the radius client |
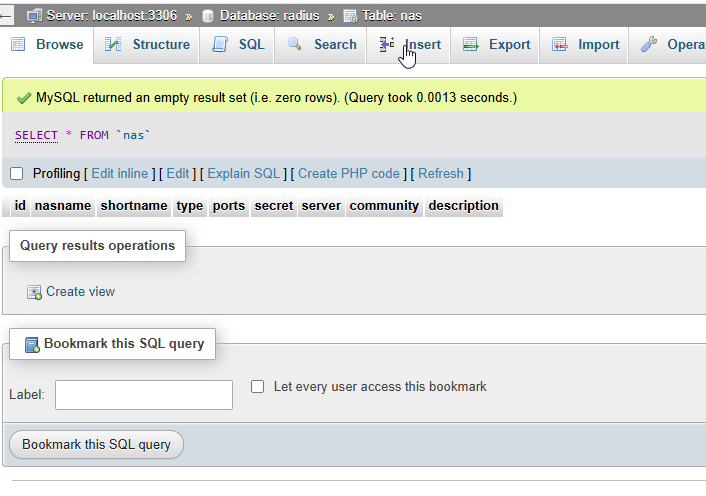
The IP of the machine I’ll test from is 10.2.0.6
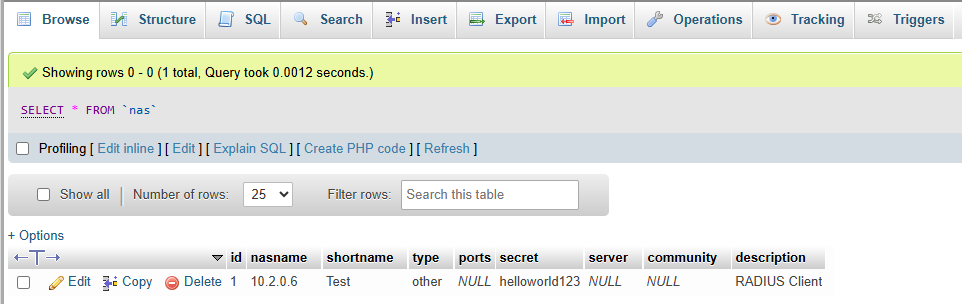
Now we add the client details, which is the device attempting to connect to the service we need the radius for, such as WiFi client or PPPoE client router.
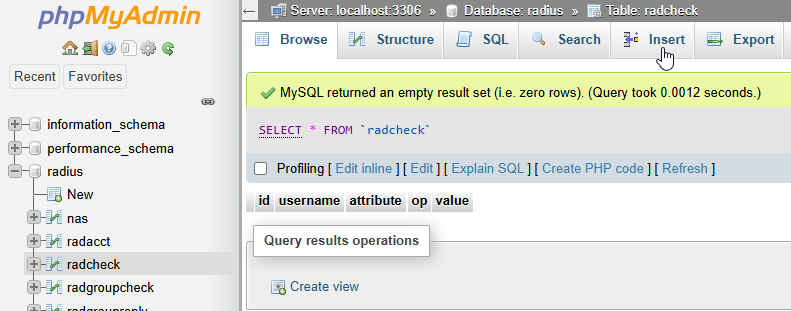
On the radcheck table, click Insert. Add the following cells:
| username: Username of the client attribute: Cleartext-Password op: := value: The password of the client |
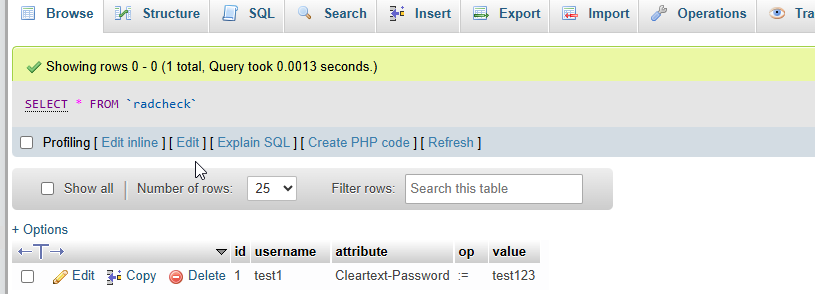
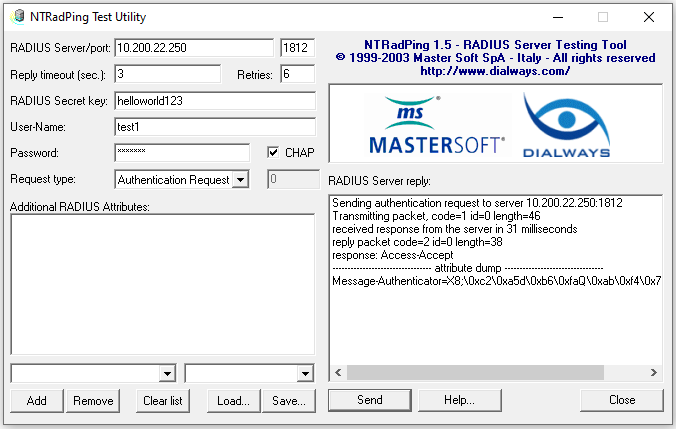
Now download the NTRadPing Utility and use the details created before:
| RADIUS Server: IP of the Radius Server Port: 1812 RADIUS Secret key: The NAS secret set User-Name: The username in the radcheck table Password: The password in the radcheck table |
Then if we get the response: Access-Accept then we have made a successful test


Greate Job Sir Thanks