In MikroTik Port Forwarding NAT rules, the dstnat chain and dst-nat action are part of the process of handling destination NAT (port forwarding). Here’s what they mean:
MikroTik Port Forwarding Overview
dstnat in the chain
- The
dstnatchain is used for processing packets that are destined for the router itself (incoming traffic). - It matches packets that are coming to a specific destination IP address and port on the router.
- It’s commonly used for traffic that needs to be forwarded to an internal device (e.g., a web server, game server, etc.).
For example:
- If an external device connects to your public IP (
WAN IP) on port 80, thedstnatchain can be used to “redirect” or “forward” that traffic to an internal private IP address, like a web server at192.168.1.10.
dst-nat in the action
- The
dst-nataction is what performs the actual destination NAT. - It changes the destination IP address (and optionally port) of the incoming packet to point to a different internal IP/port.
- This is what makes port forwarding work.
When you set the action to dst-nat, the router rewrites the destination address in the packet and forwards it to the specified internal host.
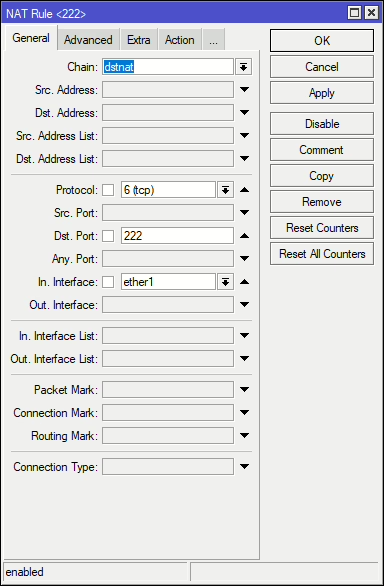
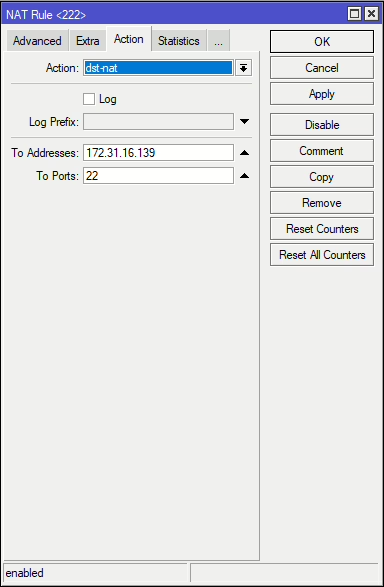
Example 1: Port Translation
This rule allows traffic hitting the router on ether1 (our WAN/Internet) interface on port 222, then translates it to 22 and forwards it to 172.31.16.139.
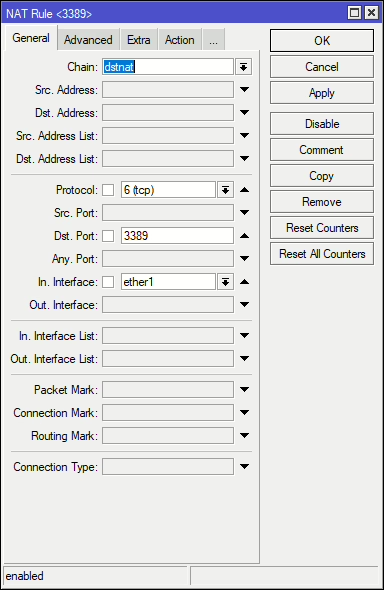
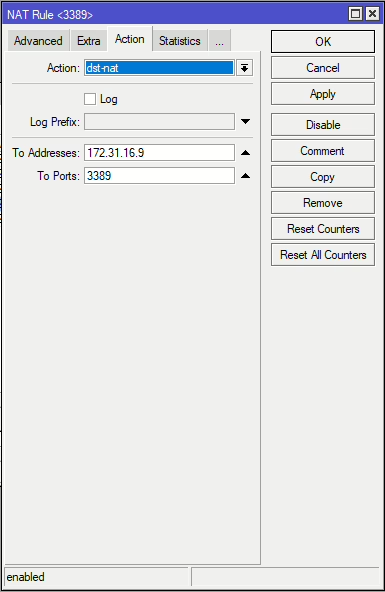
Example 2: Same Port
This option uses the same port (RDP 3389) the traffic is received on and forwards it to internal IP of 172.31.16.9.
Extra NAT for unreachable devices
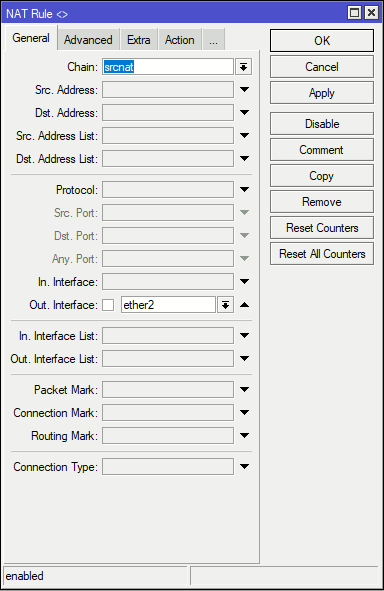
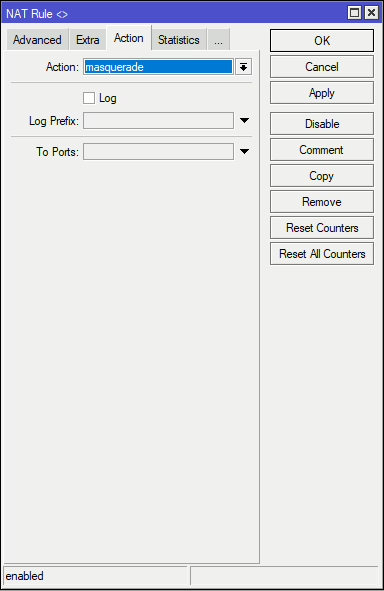
If there’s a device on the network that either does not have a gateway or the incorrect gateway set, then we can remotely reach the device by assing a Masquerade NAT rule in for the outgoing interface of the network the device is on. Providing we have an IP address on the MikroTik that can reach the device, we can NAT our traffic behind that IP (i.e Masquerading it).
This rule is the same as the same as the one we use for our outbound internet traffic except we are not using the Internet/WAN interface.
Other Firewall examples can be found here: https://www.youtube.com/watch?v=B6GEYy7nFyU