With Static Gateways
There is a second instance of this solution here whereby we apply the same config and logic as in this article however with getting the default gateway routes dynamically instead of statically, as we have here.
The Ultimate MikroTik Internet Failover #2
Initial Config
The configuration for this topology is very simple, we have the following variants:
LAN
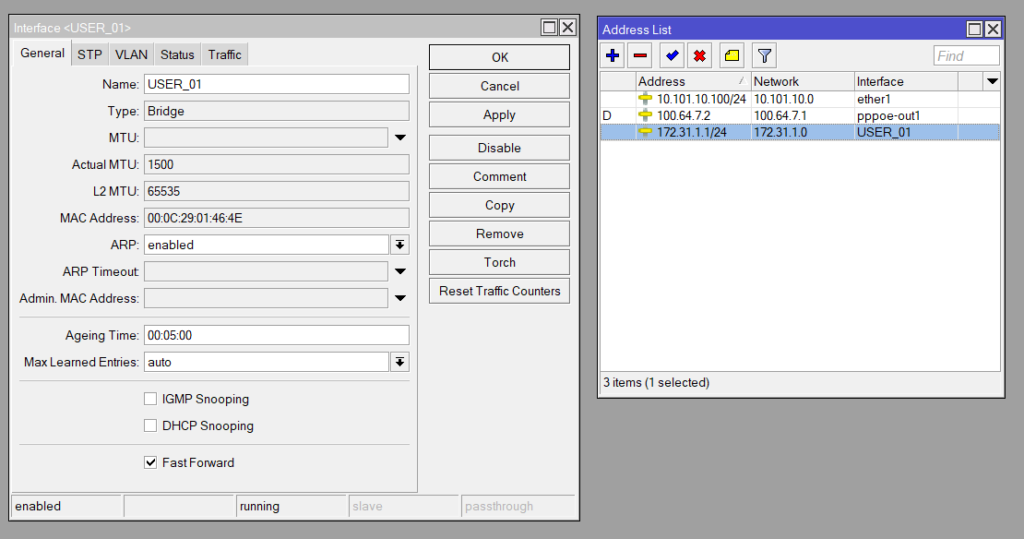
The LAN is Bridge with an IP and DHCP server running on it with a single client attached.
| Interface: Bridge Name: USER01 IP Address: 172.31.1.1/24 |
WAN1
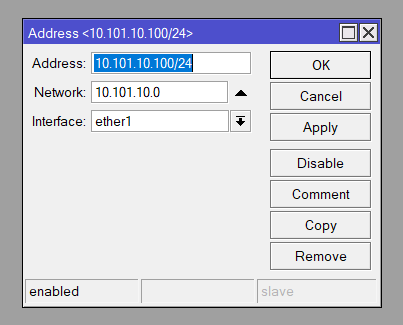
WAN1 is a simple static IP assignment.
| Interface: ether1 IP Address: 10.100.10.100/24 IP Assignment: Static |
WAN2
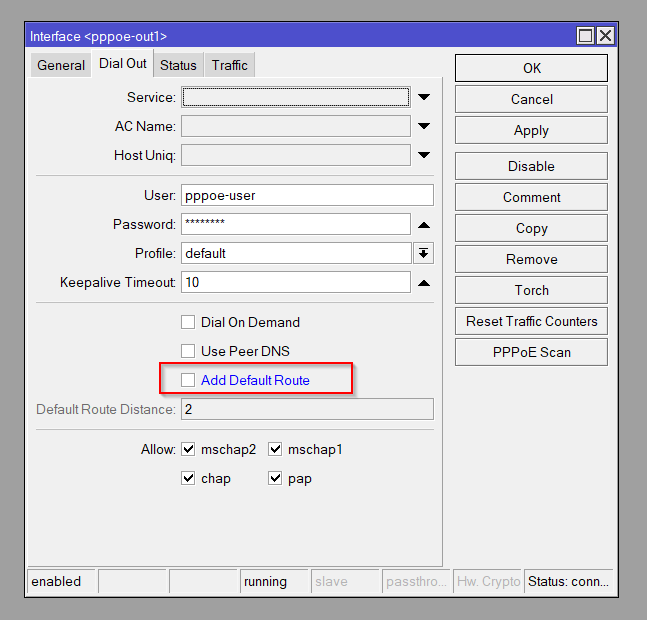
WAN2 is a PPPOE client which is common with some ISPs. It gets it’s IP dynamically from the ISP NTU (PPPOE Server) however instead of getting it’s default route we have disabled this option and will be using static routes.
| Interface: pppoe-client IP Address: 100.64.7.2 IP Assignment: Dynamic (Add Default Route: No) |
NAT
There are two separate NAT Masuerade rules for each outbound WAN interface
/ip firewall nat
add action=masquerade chain=srcnat out-interface=ether1
add action=masquerade chain=srcnat out-interface=pppoe-client1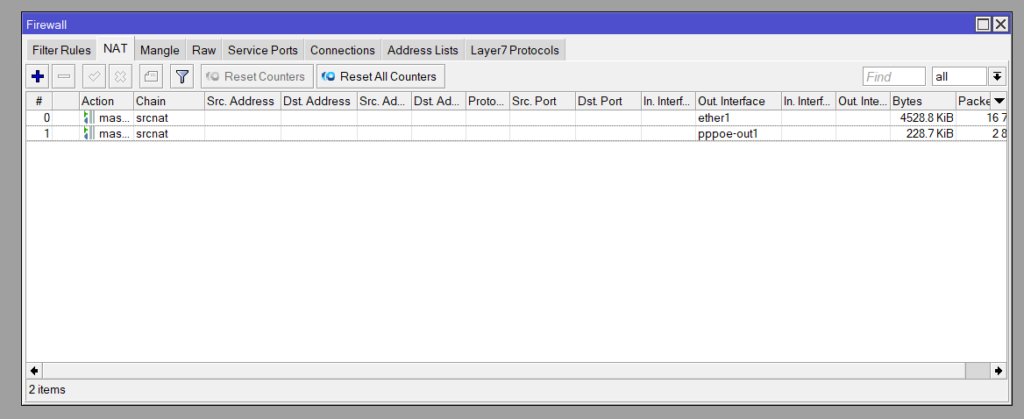
Routing
For this we will use 2 Static Default routes for both WAN1 and WAN2, with WAN1 having a distance of 1 and WAN2 having 2. This means WAN1 will be prioritised.
On each route we have added comments for each one:
- WAN1: primary_route
- WAN2: secondary_route
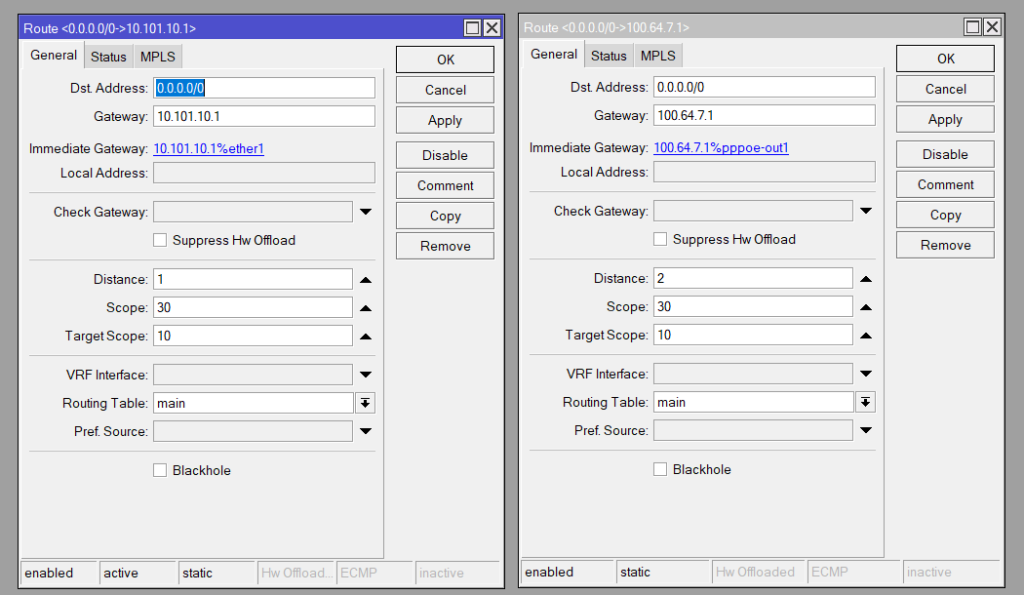
/ip route
add comment=primary_route disabled=no distance=1 dst-address=0.0.0.0/0 \
gateway=10.101.10.1 routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add comment=secondary_route disabled=no distance=2 dst-address=0.0.0.0/0 \
gateway=100.64.7.1 routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10Scripts
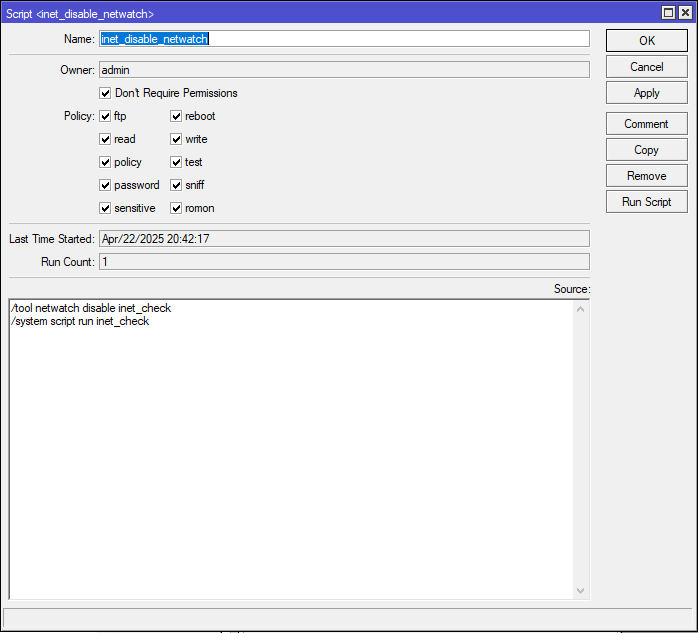
/tool netwatch disable inet_check
/system script run inet_check/system script
add dont-require-permissions=yes name=inet_disable_netwatch owner=admin policy=ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source="/tool netwatch disable inet_check\r\
\n/system script run inet_check\r\
\n"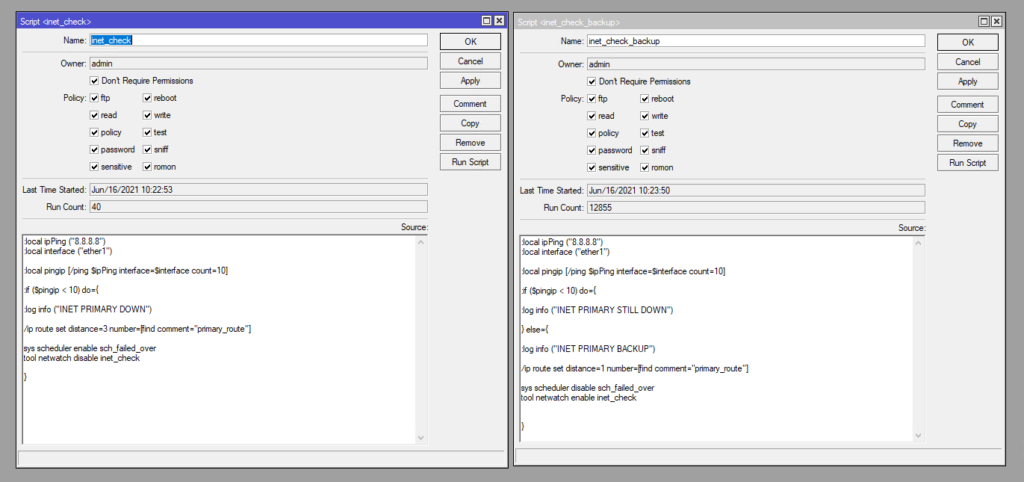
:local ipPing ("8.8.8.8")
:local interface ("ether1")
:local pingip [/ping $ipPing interface=$interface count=10]
:if ($pingip < 10) do={
:log info ("INET PRIMARY DOWN")
/ip route set distance=3 number=[find comment="primary_route"]
sys scheduler enable sch_failed_over
tool netwatch disable inet_check
}/system script
add dont-require-permissions=yes name=inet_check owner=admin policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source=":\
local ipPing (\"8.8.8.8\")\r\
\n:local interface (\"ether1\")\r\
\n\r\
\n:local pingip [/ping \$ipPing interface=\$interface count=10]\r\
\n\r\
\n:if (\$pingip < 10) do={\r\
\n\r\
\n:log info (\"INET PRIMARY DOWN\")\r\
\n\r\
\n/ip route set distance=3 number=[find comment=\"primary_route\"] \r\
\n\r\
\nsys scheduler enable sch_failed_over\r\
\ntool netwatch disable inet_check\r\
\n\r\
\n}":local ipPing ("8.8.8.8")
:local interface ("ether1")
:local pingip [/ping $ipPing interface=$interface count=10]
:if ($pingip < 10) do={
:log info ("INET PRIMARY STILL DOWN")
} else={
:log info ("INET PRIMARY BACKUP")
/ip route set distance=1 number=[find comment="primary_route"]
sys scheduler disable sch_failed_over
tool netwatch enable inet_check
}add dont-require-permissions=yes name=inet_check_backup owner=admin policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source=":\
local ipPing (\"8.8.8.8\")\r\
\n:local interface (\"ether1\")\r\
\n\r\
\n:local pingip [/ping \$ipPing interface=\$interface count=10]\r\
\n\r\
\n:if (\$pingip < 10) do={\r\
\n\r\
\n:log info (\"INET PRIMARY STILL DOWN\")\r\
\n\r\
\n} else={\r\
\n\r\
\n:log info (\"INET PRIMARY BACKUP\")\r\
\n\r\
\n/ip route set distance=1 number=[find comment=\"primary_route\"] \r\
\n\r\
\nsys scheduler disable sch_failed_over\r\
\ntool netwatch enable inet_check\r\
\n\r\
\n\r\
\n}"Netwatch
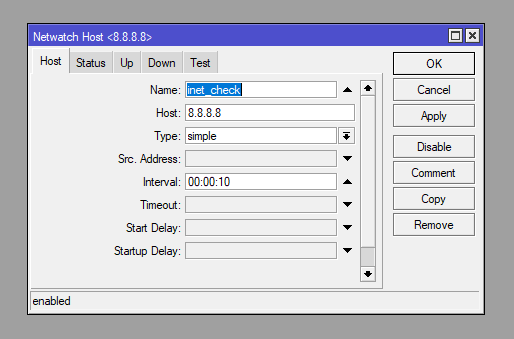
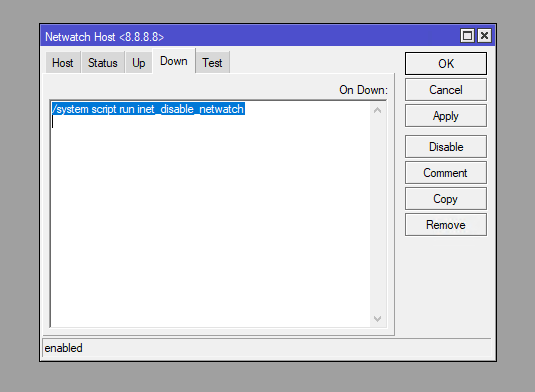
/tool netwatch
add disabled=no down-script="/system script run inet_disable_netwatch\r\
\n" host=8.8.8.8 http-codes="" interval=10s name=inet_check test-script="" type=simple up-script=""Schedular
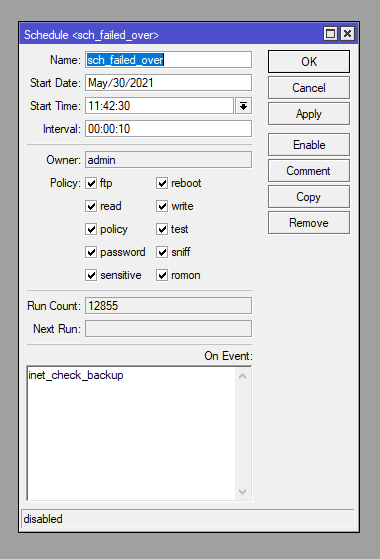
/system scheduler
add disabled=yes interval=10s name=sch_failed_over on-event=inet_check_backup \
policy=ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=2021-05-30 start-time=11:42:30

Hi – you still have ‘tool netwatch disable inet_check’ at the bottom of your inte_check script. You have already disabled it in inet_disable_netwatch.
Thank you, I shall address this shortly
So without the 8.8.8.8 static route and attempting to ping (testing against the secondary interface) using the interface option in the ping tool (like you use in your scripts) it fails. I am unsure if this will work against the primary during the inet_check_backup script that also uses the “interface=” option. Am I correct in my understanding that you have removed the 8.8.8.8 static routes from this tutorial?
Yes correct, in the end I decided they were not needed, when the Netwatch is checking it’s during a time when the primary is up so will use the defautl route (via the primary). When it is failed over and Netwatch is disabled, the we only care about checking if the primary has come back and that is done but using the interface= option on the ping command in the inet_check_backup script. We want clients to still be able to route to 8.8.8.8 in either states of failover so using static /32 routes pointing to an interface with no network access would break this.