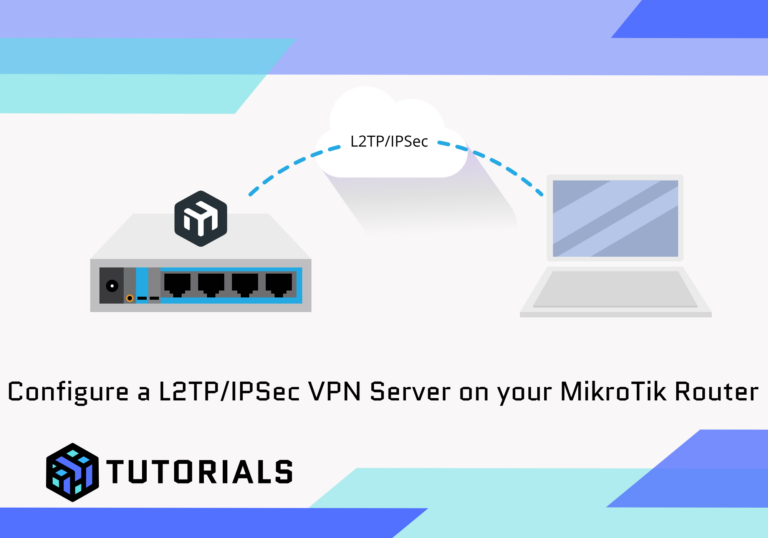
Purpose and Reason for Using a L2TP VPN
An L2TP VPN (Virtual Private Network) creates a secure and encrypted connection between devices across the internet. It is often used for:
- Privacy and Security: Encrypts data, ensuring secure communication over public or untrusted networks like Wi-Fi.
- Remote Access: Allows users to securely access private networks (e.g., company resources) from remote locations.
- Geolocation Masking: Lets users appear to access the internet from a different location.
- Bypassing Restrictions: Helps access services or websites that may be blocked or restricted geographically.
For businesses or individuals, setting up a VPN server on a MikroTik router enables secure access to the home or office network, allowing remote workers or devices to communicate securely.
This process can be configured on any MikroTik RouterOS device as long as it has direct internet connectivity. One option is to deploy a VPN server on a MikroTik CHR instance in AWS, for more info on this click here.
Step 1: Configure the IP Pool for VPN Clients
- Purpose: Defines the range of IP addresses to assign to VPN clients when they connect.
- Reason: Each connected device needs a unique IP address to communicate with the network. This ensures VPN clients can operate in their own subnet and not interfere with existing devices.
- Log in to your MikroTik router using WinBox or via SSH.
- Navigate to IP > Pool.
- Click Add (
+), and set:- Name:
VPN_Pool - Addresses:
192.168.88.100-192.168.88.200(replace with your desired range).
- Name:
- Click OK.
Step 2: Create a PPP Profile for VPN Clients
- Purpose: Sets up the specific configuration that applies to all VPN users, such as IP addressing, DNS servers, and other parameters.
- Reason: Profiles simplify management by applying consistent settings to all users, such as routing traffic through specific subnets or setting up DNS servers for client devices.
- Go to PPP > Profiles.
- Click Add (
+), and configure:- Name:
L2TP_Profile - Local Address: Enter the router’s IP address (e.g.,
192.168.88.1). - Remote Address: Select the
VPN_Poolcreated earlier. - DNS Server: Enter the DNS servers (e.g.,
8.8.8.8, 8.8.4.4).
- Name:
- Click OK.
Step 3: Add L2TP Users
- Purpose: Creates individual accounts with unique usernames and passwords for VPN users.
- Reason: Ensures secure and controlled access to the VPN. Each user must authenticate before gaining access, providing accountability and the ability to manage permissions individually.
- Go to PPP > Secrets.
- Click Add (
+), and configure:- Name: Enter the VPN username (e.g.,
user1). - Password: Enter the VPN password.
- Service: Set to
l2tp. - Profile: Select
L2TP_Profile.
- Name: Enter the VPN username (e.g.,
- Click OK.
- Repeat for additional users if needed.
Step 4: Configure the L2TP Server
- Purpose: Enables and configures the L2TP service on the router, allowing it to accept incoming L2TP VPN connections.
- Reason: The L2TP server is the core component that manages client connections. Without enabling it, the router won’t accept or process VPN requests.
- Go to PPP > Interfaces > L2TP Server.
- Click Enabled to activate the server.
- Click Settings, and configure:
- Default Profile: Select
L2TP_Profile. - Authentication: Check
MSCHAP2andMSCHAP1.
- Default Profile: Select
- Click OK.
Step 5: Configure IPsec
- Purpose: Secures the L2TP connection with IPsec, which encrypts data and ensures it cannot be intercepted or tampered with.
- Reason: L2TP on its own does not encrypt traffic. IPsec adds a layer of encryption and security, which is essential for secure communication over the internet.
- Navigate to IP > IPsec > Proposals.
- Select the default proposal, and ensure:
- Auth Algorithms:
sha1. - Enc Algorithms:
aes-128and3des.
- Auth Algorithms:
- Go to IP > IPsec > Peers, and click Add (
+):- Address:
0.0.0.0/0(for any remote client). - Auth Method:
pre-shared key. - Secret: Enter your PSK (e.g.,
MySecretKey). - Exchange Mode:
main.
- Address:
- Click OK.
Step 6: Firewall and NAT Configuration
Allow L2TP and IPsec Traffic:
- Purpose: Opens the necessary ports and protocols on the router to allow VPN traffic to pass through.
- Reason: Without these rules, the router may block VPN traffic, preventing clients from connecting.
Masquerade VPN Clients:
- Purpose: Configures NAT (Network Address Translation) for VPN clients, enabling them to access the internet through the router.
- Reason: Ensures that VPN clients can communicate with external networks while appearing to originate from the router’s IP address.
- Allow L2TP and IPsec Traffic:
- Navigate to IP > Firewall > Filter Rules.
- Add the following rules:
- Rule 1: Allow UDP 500 (IPsec).
- Chain:
input - Protocol:
udp - Dst. Port:
500
- Chain:
- Rule 2: Allow UDP 4500 (IPsec).
- Chain:
input - Protocol:
udp - Dst. Port:
4500
- Chain:
- Rule 3: Allow IPsec ESP.
- Chain:
input - Protocol:
ipsec-esp
- Chain:
- Rule 4: Allow L2TP (UDP 1701).
- Chain:
input - Protocol:
udp - Dst. Port:
1701.
- Chain:
- Rule 1: Allow UDP 500 (IPsec).
- Masquerade VPN Clients:
- Go to IP > Firewall > NAT, and click Add (
+). - Set:
- Chain:
srcnat - Out. Interface: Your WAN interface.
- Action:
masquerade.
- Chain:
- Go to IP > Firewall > NAT, and click Add (
Step 7: Test the Configuration
- Purpose: Validates that the VPN setup is working as intended by connecting a client device and testing connectivity.
- Reason: Testing ensures that the configuration is correct, and VPN clients can connect, receive the right IP address, and access network resources securely.
- On a client device, configure the VPN:
- Server: Router’s public IP or domain.
- VPN Type:
L2TP/IPsec PSK. - PSK: Enter the Pre-Shared Key.
- Username and Password: Use credentials created in Step 3.
- Connect and verify:
- Ensure the client gets an IP address from the
VPN_Pool. - Test internet and local resource access.
- Ensure the client gets an IP address from the
Notes
- Ensure the router’s public IP is accessible (check NAT and ISP configurations).
- If using a firewall or NAT device upstream, forward UDP ports 500, 4500, and 1701 to the MikroTik router.
- Use secure PSK, username, and password for better security.
Why This Configuration is Effective
This setup uses:
- L2TP/IPsec: A secure VPN protocol suitable for most devices (Windows, macOS, Android, iOS).
- Separate Subnet: Isolates VPN clients, enhancing security and managing traffic efficiently.
- Pre-Shared Key and Authentication: Adds layers of security, ensuring only authorized users can connect.
By following this guide, you can create a secure and reliable VPN server for personal or business use. For more information visit MikroTik.com